exp | Unix Timestamp | Yes | Date and time of token expiration. Default expiration time is 24 hours. You can change expiration time for every Login project. |
iss | string | Yes | Service that signed the token: https://login.xsolla.com. |
iat | Unix Timestamp | Yes | Date and time of giving the token. |
sub | string (UUID) | Yes | User ID written on the Xsolla Login server side. |
groups | array | Yes | List of groups the user is in. Each group: id — group ID; name — group name; is_default — whether the group is default (true or false). There can be only one default group, which initially includes all users before they are distributed into different groups. |
xsolla_login_project_id | string (UUID) | Yes | Login project ID. |
type | string | | Authentication option: xsolla_login — login via username/email and password; social — social login; email — passwordless login via one-time code by email; phone — by SMS; firebase — Firebase storage; playfab — PlayFab storage; proxy — custom storage; device — device ID; server_custom_id — custom ID. |
avatar | string | | User avatar URL. |
username | string | | Username. |
publisher_id | integer | | ID of a merchant who owns a Login project. |
email | string | | User email address. |
payload | string | | Additional information that is passed in the payload parameter during authentication. |
promo_email_agreement | boolean | | true if the user agrees to receive a newsletter, false otherwise. Default: true. To add to the Login widget registration form: contact your Account Manager (Widget 2.0) or add the fields parameter with the promo_email_agreement value to the initialization code (previous widget version). |
connection_information | string | | Shows whether the user confirmed their birth date or not. Confirmation is made via the okname service. |
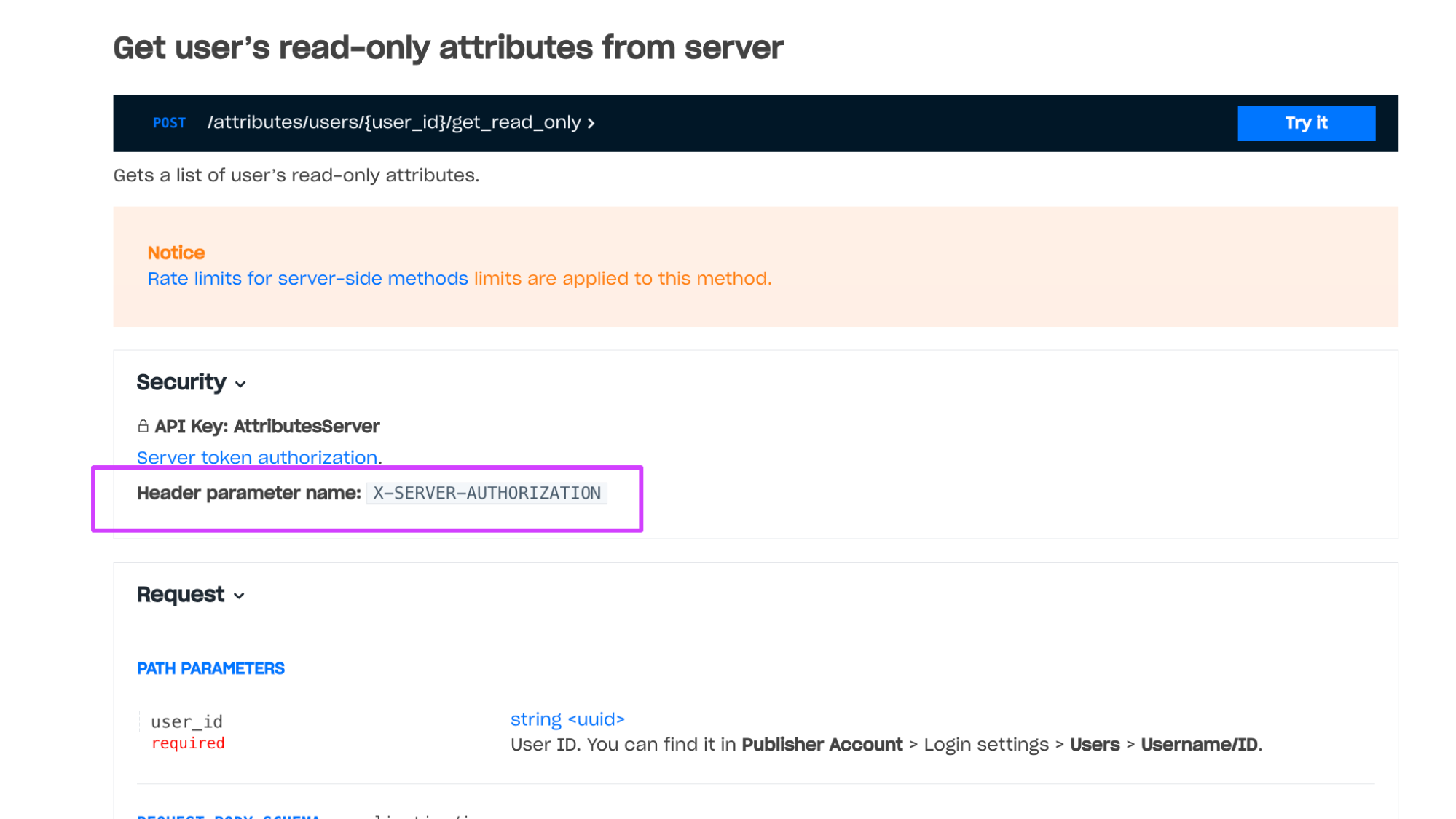 Example of a method with client-side authentication:
Example of a method with client-side authentication: 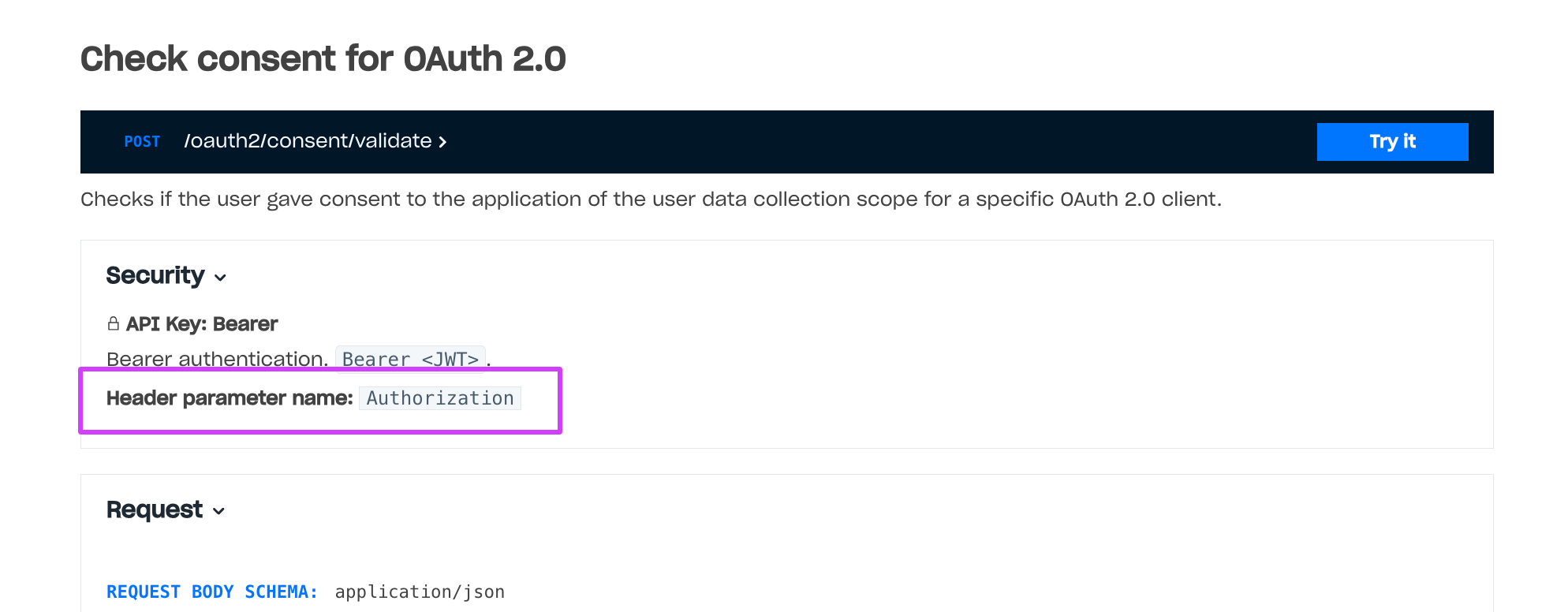
Claims that are contained in the token after authentication via a social network. Presence of these claims does not depend on the user database.
provideridis_cross_authsocial_access_tokenaccess_tokenparameter used for authentication. Contact your Account Manager to set up the feature.picturebirthdaygendername